Aws console login: 5 Easy Steps to Master AWS Console Login Like a Pro
Logging into the AWS Console doesn’t have to be complicated. Whether you’re a beginner or brushing up on your cloud skills, this guide breaks down everything you need to know about the aws console login process—securely, efficiently, and without confusion.
What Is the AWS Console and Why Is Login Important?

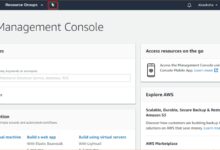
The AWS Management Console is a web-based interface that allows users to interact with Amazon Web Services (AWS) offerings such as EC2, S3, Lambda, and RDS. It provides a visual, user-friendly way to manage cloud infrastructure, monitor resources, and configure security settings. The aws console login is your gateway to this powerful ecosystem.
Understanding the Role of the AWS Console
The AWS Console acts as the central hub for managing your cloud environment. After completing the aws console login, users gain access to over 200 services that support computing, storage, networking, machine learning, and more. It’s designed for developers, system administrators, and businesses looking to scale their operations in the cloud.
- Provides a graphical interface for managing AWS resources
- Supports real-time monitoring and alerts
- Enables integration with third-party tools and APIs
Unlike command-line tools or SDKs, the console is ideal for users who prefer point-and-click navigation. However, it’s important to note that while the interface simplifies operations, incorrect configurations post-login can lead to security risks or unexpected charges.
Why Secure AWS Console Login Matters
Because the AWS Console grants access to critical infrastructure, securing the aws console login process is non-negotiable. A compromised account can lead to data breaches, unauthorized resource usage, or even cryptojacking. AWS recommends enabling Multi-Factor Authentication (MFA), using IAM roles instead of root credentials, and regularly auditing access logs.
“The root user has unrestricted access to all AWS services and resources in the account. Never use it for daily tasks.” — AWS Security Best Practices
Ensuring a secure aws console login isn’t just about entering the right username and password—it involves identity management, access policies, and compliance with organizational security standards.
Step-by-Step Guide to AWS Console Login
Performing an aws console login is straightforward, but understanding each step ensures you avoid common pitfalls. Whether you’re logging in as a root user or an IAM user, the process varies slightly. Let’s walk through the correct procedure.
Step 1: Navigate to the AWS Sign-In Page
Open your preferred web browser and go to the official AWS sign-in URL: https://aws.amazon.com/console/. This is the primary entry point for the aws console login. Avoid using third-party links or bookmarks from untrusted sources to prevent phishing attacks.
On the homepage, click on “Sign In to the Console” located at the top right corner. This redirects you to the AWS sign-in portal where you’ll choose between logging in as a root user or an IAM user.
Step 2: Choose Your Login Type
You’ll see two options:
- Root User: The account created when you first signed up for AWS. It has full administrative privileges.
- IAM User: A user created by an administrator with specific permissions.
If you’re logging in for the first time after account creation, you may need to use your root user email. However, AWS strongly advises against using the root user for routine tasks. Instead, create IAM users with limited permissions.
Step 3: Enter Your Credentials
After selecting your login type, enter your credentials:
- For root users: Enter the email address used during account registration and the password.
- For IAM users: Enter your account ID or alias and your IAM username and password.
The account ID is a 12-digit number assigned by AWS. Alternatively, you can use a custom account alias if one has been set up by your administrator. Always double-check the spelling and case sensitivity of your username.
Step 4: Complete Multi-Factor Authentication (MFA)
If MFA is enabled—which it should be—you’ll be prompted to enter a time-based one-time password (TOTP) from your authenticator app (like Google Authenticator or Authy) or a hardware key. This adds a critical layer of security to the aws console login process.
Without MFA, your account is vulnerable to brute-force attacks and credential stuffing. AWS offers virtual and U2F security keys for enhanced protection. Learn more about setting up MFA at AWS MFA Documentation.
Step 5: Access the AWS Dashboard
Once authenticated, you’ll be redirected to the AWS Management Console dashboard. From here, you can navigate to services via the search bar or the services menu. The dashboard displays recent activity, billing alerts, and service health status.
Take a moment to review the region selector in the top-right corner. AWS operates in multiple geographic regions, and your resources are region-specific. Always confirm you’re working in the correct region to avoid misconfigurations.
Common Issues During AWS Console Login and How to Fix Them
Even experienced users encounter issues during the aws console login process. From forgotten passwords to MFA failures, these problems can disrupt workflows. Here’s how to troubleshoot the most frequent login errors.
Forgot Password or Locked Account
If you’ve forgotten your password, click on “Forgot Password?” on the login page. You’ll be prompted to enter your email or account ID. AWS will send a reset link to the registered email address.
For IAM users, only the account administrator can reset passwords. Root users can reset their own passwords. If your account is locked due to multiple failed attempts, wait 15–30 minutes before retrying, or contact AWS Support.
Incorrect Account ID or Alias
Entering the wrong account ID or alias is a common mistake. Remember:
- The account ID is 12 digits long (e.g., 123456789012).
- The account alias is a custom name (e.g., my-company-aws).
If you don’t know your account ID, the root user can find it by logging in and checking the top-right dropdown menu. IAM users should contact their administrator for this information.
MFA Device Not Working
If your MFA app isn’t generating codes or your hardware key is lost, you may be locked out. AWS allows backup methods such as:
- Recovery codes (if previously saved)
- Alternate MFA devices (if configured)
- Contacting AWS Support with identity verification
To prevent this, always register at least two MFA methods. AWS also supports FIDO2 security keys for passwordless authentication, reducing dependency on apps.
Best Practices for Secure AWS Console Login
Security should be the top priority when performing an aws console login. A single compromised credential can lead to massive data exposure or financial loss. Follow these best practices to protect your AWS environment.
Never Use Root User for Daily Tasks
The root user has unrestricted access to every resource and billing information. AWS recommends creating IAM users with the principle of least privilege. Assign roles and policies that limit access to only what’s necessary.
“Use the root user only to create your first IAM user and to perform a few account-specific tasks.” — AWS IAM User Guide
After setting up IAM users, lock away the root credentials and enable MFA on the root account immediately.
Enable Multi-Factor Authentication (MFA) for All Users
MFA is one of the most effective ways to secure the aws console login. It requires two forms of identification: something you know (password) and something you have (MFA device). AWS supports:
- Virtual MFA apps (Google Authenticator, Microsoft Authenticator)
- Hardware MFA devices (YubiKey, Feitian)
- U2F security keys
You can enforce MFA through IAM policies. For example, use a service control policy (SCP) in AWS Organizations to require MFA for sensitive actions like changing IAM roles or accessing S3 buckets.
Use Strong Password Policies
Weak passwords are a leading cause of account breaches. AWS allows you to set password policies at the account level, including:
- Minimum length (12+ characters recommended)
- Requirement for uppercase, lowercase, numbers, and symbols
- Password expiration (90 days)
- Prevention of password reuse
These policies can be configured under IAM > Account Settings. Enforce them across all IAM users to maintain consistency.
How to Set Up IAM Users for AWS Console Login
Creating IAM users is essential for team collaboration and access control. Instead of sharing root credentials, administrators should create individual IAM accounts with tailored permissions. Here’s how to do it right.
Create a New IAM User
Log in as the root user or an administrator IAM user. Navigate to the IAM Console. Click on “Users” in the left sidebar, then “Create User”.
Enter a username (e.g., john-dev) and select “AWS Management Console access”. Choose whether to let the user create their own password or set one for them. For security, require password reset on first login.
Assign Permissions to the IAM User
After creating the user, assign permissions using one of three methods:
- Add to Group: Assign the user to a group with predefined policies (e.g., Developers, Admins).
- Attach Policies Directly: Apply specific policies like AmazonS3ReadOnlyAccess.
- Copy Permissions from Existing User: Useful for onboarding similar roles.
Always follow the principle of least privilege. For example, a developer might need EC2 and Lambda access but not IAM or billing permissions.
Provide Login Instructions to the User
Once the user is created, AWS provides a sign-in URL in the format: https://[account-id].signin.aws.amazon.com/console. Share this link along with the username. The user will set their password upon first login.
Encourage them to enable MFA immediately. You can automate this using AWS Lambda and EventBridge to send reminders or enforce MFA via policy.
Using AWS Single Sign-On (SSO) for Centralized Login
For organizations managing multiple AWS accounts, AWS Single Sign-On (SSO) simplifies the aws console login process. It allows users to log in once and access multiple accounts and applications using federated identities.
What Is AWS SSO?
AWS SSO is an identity management service that enables centralized access control across AWS accounts and third-party applications. It integrates with Microsoft Active Directory, Azure AD, and other identity providers (IdPs) via SAML 2.0.
Instead of managing IAM users in each account, administrators can define permissions sets and assign them to users or groups through AWS SSO. This reduces administrative overhead and improves security posture.
How AWS SSO Enhances Login Experience
With AWS SSO, users visit the AWS SSO portal, log in with their corporate credentials, and choose which account and role to assume. This eliminates the need to remember multiple usernames and passwords.
- Single dashboard for all accessible AWS accounts
- Federated access using existing enterprise identities
- Support for MFA and conditional access policies
It’s especially useful for large enterprises using AWS Organizations. Learn more at AWS SSO Overview.
Setting Up AWS SSO
To configure AWS SSO:
- Go to the AWS SSO console.
- Enable AWS SSO in your organization.
- Connect your identity source (e.g., AWS SSO directory or external IdP).
- Create permission sets (e.g., PowerUserAccess).
- Assign users or groups to accounts with specific roles.
After setup, users access https://[your-sso-portal].awsapps.com and log in with their corporate email and password. They can then switch between roles seamlessly.
Advanced Tips for Managing AWS Console Sessions
Once you’ve completed the aws console login, managing your session effectively improves productivity and security. Here are advanced techniques for optimizing your AWS Console experience.
Customize Your Console Dashboard
The AWS Console dashboard is customizable. You can add widgets for specific services, set up cost alerts, or pin frequently used resources. This reduces navigation time and keeps critical information visible.
To customize, click the “Customize” button on the dashboard. Add items like “Cost Explorer”, “CloudWatch Alarms”, or “Recent Resources”. Save your layout for future sessions.
Use Browser Profiles for Multiple Accounts
If you manage multiple AWS accounts (e.g., development, staging, production), use separate browser profiles or incognito windows to avoid confusion. Each profile can stay logged into a different account.
Alternatively, use the AWS IAM Identity Center (formerly SSO) to switch between accounts without logging out. Bookmark the direct login URLs for each account to streamline access.
Monitor Active Sessions and Sign Out Remotely
AWS does not automatically log you out after a period of inactivity. Always manually sign out when using shared or public computers. You can also monitor active sessions via CloudTrail logs.
If you suspect unauthorized access, use IAM to rotate credentials, disable access keys, or delete sessions. While AWS doesn’t offer a “sign out all devices” feature for the console, you can invalidate temporary credentials via the CLI.
What is the URL for AWS Console login?
The official URL for AWS Console login is https://aws.amazon.com/console/. From there, click “Sign In to the Console” and choose your login type (root or IAM user).
How do I recover my AWS account if I can’t log in?
If you’re locked out, use the “Forgot Password?” option for password reset. If you’ve lost MFA access, contact AWS Support with proof of identity. For IAM users, the account administrator can reset credentials.
Can I use social login for AWS Console?
No, AWS does not support social logins (Google, Facebook, etc.) for the AWS Management Console. Authentication is done via AWS credentials, IAM users, or through federated identity using AWS SSO and corporate directories.
Is it safe to save AWS login credentials in my browser?
It’s not recommended to save AWS credentials in your browser, especially for root or admin accounts. Browser password managers are vulnerable to malware and phishing. Use a dedicated password manager and always enable MFA for an extra layer of security.
How can I automate AWS Console login?
You cannot automate the web-based aws console login directly due to security restrictions. However, you can use AWS CLI, SDKs, or IAM roles for programmatic access. For browser automation, consider AWS IAM Identity Center with SSO integration.
Mastering the aws console login is the first step toward effective cloud management. From secure authentication and IAM user setup to leveraging AWS SSO and troubleshooting common issues, this guide has covered every aspect to ensure a smooth and safe experience. Always prioritize security by enabling MFA, avoiding root user usage, and following AWS best practices. With the right approach, your aws console login becomes not just a routine task, but a secure gateway to limitless cloud possibilities.
Recommended for you 👇
Further Reading: